WEBlog - discover interesting things about your employees.
All posts
How to Craft and Implement an Effective Internet Usage Policy
Data leaks, databases destroyed by malware, money stolen by hackers, hostile workplace lawsuits, employee productivity downfalls, and low networks performance — what do these events have in common? They all are consequences of internet abuse in the workplace. According to a survey, 60% of respondents admit to watching porn at work, while another study says that 45% of employees log to gambling websites during working hours. It’s no wonder that 58% of organizations surveyed by Spiceworks track employee online activity on corporate networks and 89% block or limit internet access in some way.
But do employees know how they should use this modern technology to perform their best at work? If you don’t have an Internet Usage Policy adopted, your staff lacks a clear understanding of inappropriate practices they must refrain from. Yet, the first person who needs to get an in-depth insight into the rules is a policy-maker.
7 Things to Keep In Mind When Creating Your Internet Usage Policy
Consider it from different points of view
In the perfect world, an IUP should be written through the combined forces of IT, HR, and legal departments. Computer geeks know what security gaps and other technical issues should be covered in the document while legal professionals are aware of laws and regulations it has to comply with. HR specialists, in their turn, can add their knowledge of your workforce specifics to make the rules truly human-centered. If you don’t have the full panel of experts on the payroll, you can assign the task to one of the teams, but don’t leave other aspects out of account.
Customize it to your business
While the Internet is full of IUP samples, it’s not wise to grab the first available option just to have some document in place. Different business environments require different approaches, and you need to think through your needs and company structure. For example, if a company pays for internet traffic, its policy as to sending/receiving personal emails or downloading non-work media files might be tougher. On the other hand, a business with an unlimited Internet plan may choose to allow watching YouTube videos during breaks.
Educate your staff
Although an Internet Usage Policy establishes certain rules for employees to obey, it doesn’t explain why obeying them is important for both company and its staff. Surely, some things like Internet-related distractions decreasing productivity are obvious. However, other threats, such as malware infecting the company network due to employees browsing news websites, might be not that easy to understand. That’s why you should consider complementing an IUP with some kind of training sessions dedicated to web-borne threats for your team members to realize the reasoning behind the policy.
Adapt the policy to people, not vice versa
It’s a bit tricky since any policy is effective when it applies to everyone. But humans are different, and you will fail to create a productive environment in the workplace if brushing this fact off. Some of your staff members can work long hours without checking personal mailboxes or the social pages of their relatives, but others get nervous when feeling isolated from their friends and family, which affects their performance more than a 5-minute chat in a messenger. The question is whether you are ready to allow your staff to detach from work by using the corporate Internet during small breaks. A study says that you should since web browsing refreshes tired workers and enhances their productivity.
Incorporate your company’s culture into the policy
An IUP is only a part of multiple company rules regulating various aspects of workflow. Together with the company’s mission and values, they shape corporate culture, which is supposed to guide the staff towards specific performance goals that benefit the organization. But how can this guidance coordinate employees’ behavior when its different parts clash with each other? If you claim that your business is fueled by creativity, is it fair to prohibit your staff from searching for inspiration online when they are out of ideas? And if your business thrives on family values, wouldn’t it feel wrong to ban short Skype conversations with senior relatives when they are seeking help? An Internet Usage Policy is one of the practices through which a company implements its values, so make them consistent.
Find a balance
Certainly, you may choose to prohibit any personal use of your company’s resources, but would you be hunting for each small violation? Then again, if you allow accessing the Web during a lunch break, are you going to punish an employee who is 5 minutes late with switching to work? The point is that penalties must be applied to violators, which will be covered below; yet focusing on restrictions rather than on trust is the wrong way toward building a friendly environment. It’s better to provide your staff with time-controlled access to safe non-work websites and apps while signaling that you trust them as long as they are results-driven.
Be ready to impose penalties
An Internet Usage Policy needs to be clear about violations and punishments they carry. The penalties can range from a verbal or written reprimand to down-grading or firing, depending on the severity of the policy breach and whether the violations are persistent. But the sanctions recorded in the policy won’t do any good unless you are ready to enforce them. If IUP breaches are mostly ignored, your staff will take it for granted that their Internet misuse has no consequences, and the policy just won’t work.
How to Implement an Internet Usage Policy with Work Examiner
While Work Examiner provides a range of solutions to meet different business needs, each of its products is designed with acceptable Internet usage in mind. Let’s explore how they contribute to the IUP implementation through the example of Controlio.
Inappropriate websites ban
You will hardly find a company with an IUP welcoming adult content, gambling, illegal activities, or any kind of discrimination and harassment. With Controlio deployed, you can help your staff steer clear of multiple online temptations, including accidental visits to inappropriate websites, for instance, via links from seemingly innocent web platforms. You just need to specify a site in the Rules section of the Behavior tab for the app to deny access to it. It is even more convenient to apply the blocking rule to entire categories of websites thanks to WE’s 3-million domain database, which is constantly updated. By selecting the “porn”, “gambling”, “gaming”, or “aggressive” category, you shut off all the web pages with the content falling under the rule.
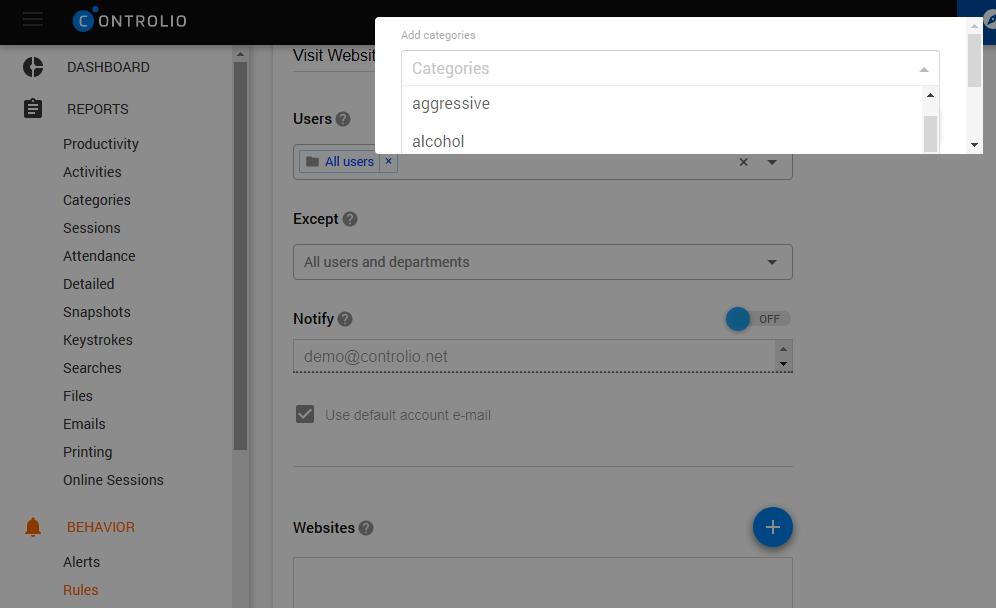
Distractive websites and apps blocking
Usually, employees are not expected to spend most of their working day socializing on Instagram or shopping online. It doesn’t matter whether you have a strict policy forbidding any non-work activities on the Web or allow for time-controlled access; rules set in Controlio will help you to drive it home to your staff. You can block separate websites and apps by entering their URLs and app or file names (such as “Skype”), respectively. Blocking by category is also available for online distractions, namely, for “dating”, “sports”, “chat”, “shopping”, and other categories.
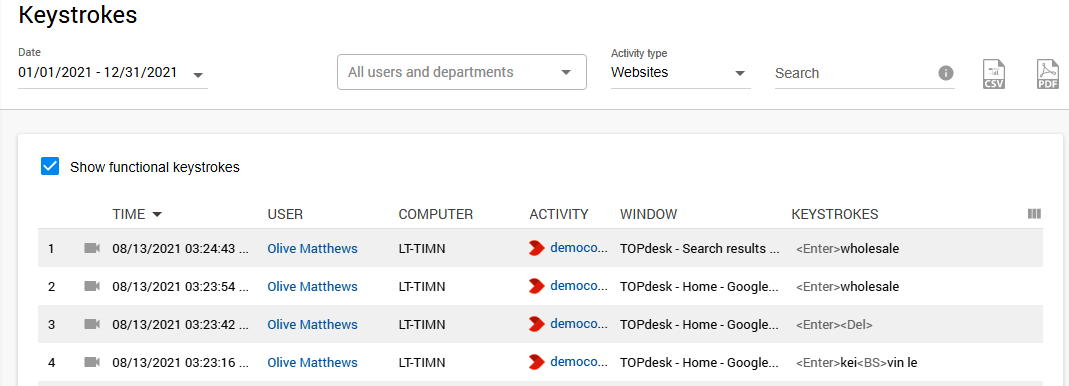
Security threats elimination
As was already mentioned, your workers may know nothing about identity theft often associated with using proxy servers or computer viruses frequently implanted into files distributed through P2P file-sharing platforms. Your IT specialists should identify the most common threats related to browsing the Web while the Controlio database has already got them covered. In addition to blocking “file share”, “threats”, “proxy”, and some other potentially dangerous categories of sites, Controlio captures and stores online searches and keystrokes. These reports help spot both security risks and online distractions.
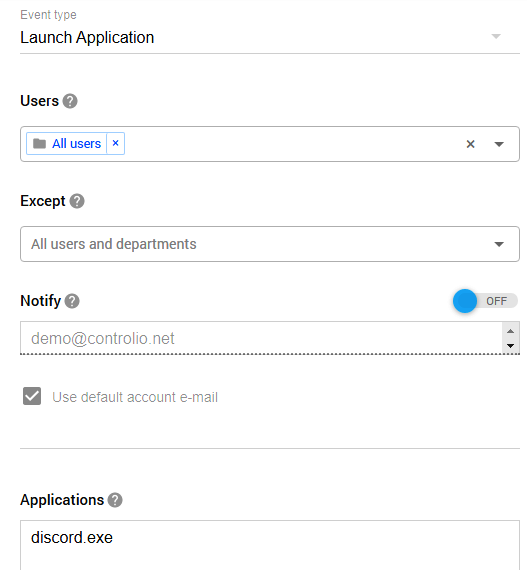
Dealing with violators
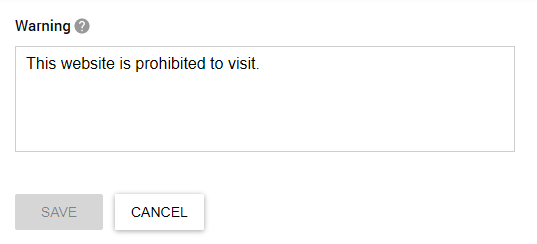
First of all, your employees are people, and people make mistakes. It is easy to forget about IUP restrictions amid a chaotic workday, so it would be honest to remind them of the rules with a warning. Controlio allows for custom messages to be displayed when a user tries to visit a prohibited website or launch a forbidden application.
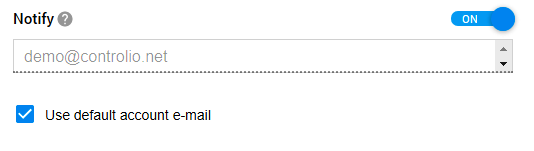
The next level of your defence is setting alerts on suspicious activities, which apply not only to websites and apps but also keystrokes. When specifying rules for these actions, you need to choose an email address for receiving notifications every time somebody breaks the rule.
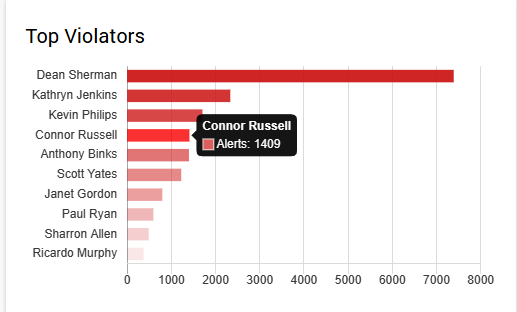
Finally, you get an automatically generated report on top violators, delivered right to your dashboard and showing the number of the alerts they earned.
Another way to explore IUP breaches is by going to the Alerts tab, which stores the names of wrongdoers, the date, type, and screen recording of the violation, and the device used for it.
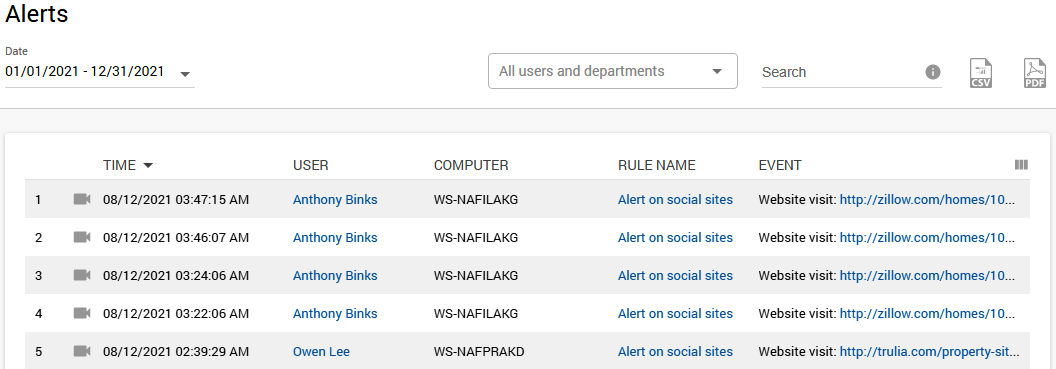
Tracking in real-time
Real-time monitoring of your staff’s online sessions gives you the power to immediately respond to any IUP violation or suspicious activity. This tab shows users who are currently online, computers they use, websites and apps launched, with the option to watch the live stream of their screens in real time. The feature equips you with all necessary pieces of information to abort the unpermitted activity and prevent further problems.
Controlled Internet access
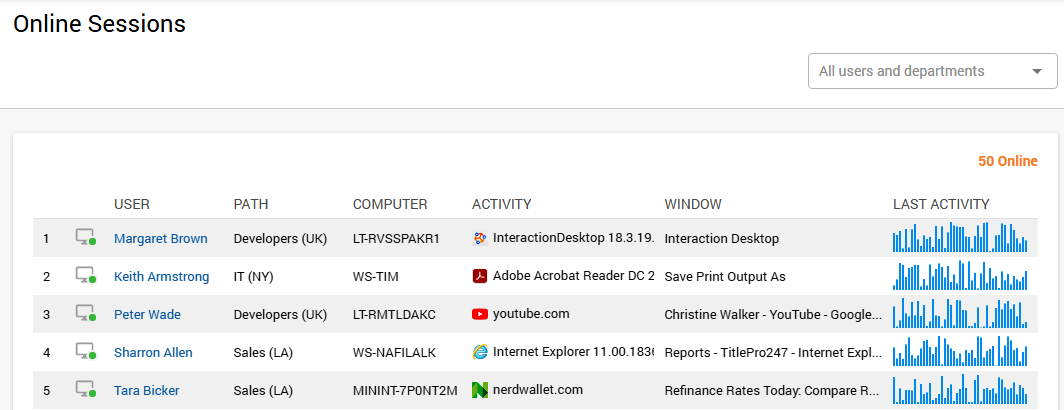
Thanks to the highly customizable nature of Work Examiner’s products, you can be very flexible with your Internet Usage Policy, applying different rules for different departments and even team members. When establishing rules for online activities, you include users and teams in the applicable list or exclude them from it as you see fit.

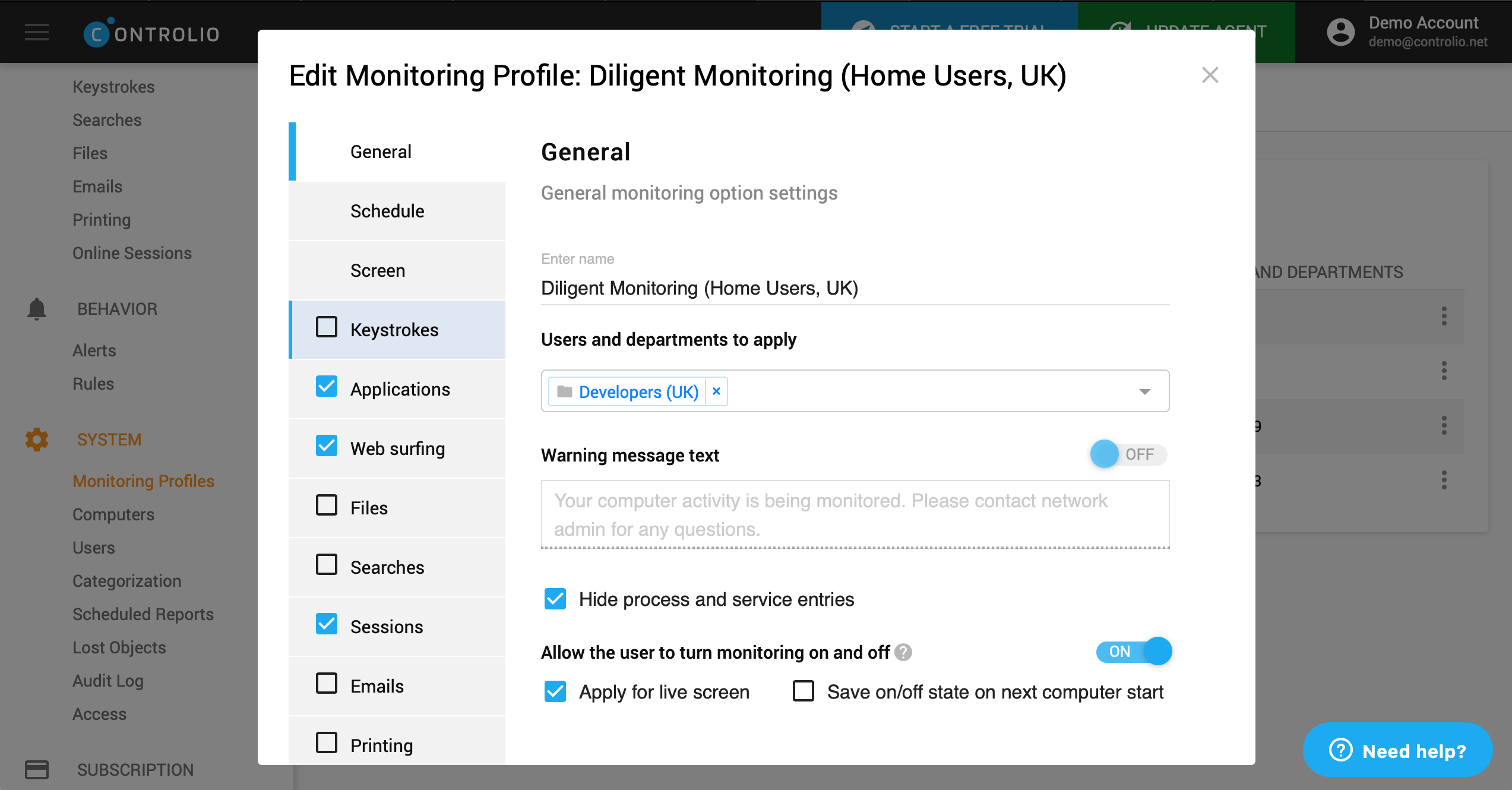
There is also another option in the Monitoring Profiles section. Here, you are free to customize each user profile for monitoring, including settings related to internet usage.
So, if you decide to allocate some online time for personal use, you are sure to enjoy this flexibility. It is even possible to adjust a warning linked to non-work websites and apps so that it reminds the users how much time they have to detach from work.
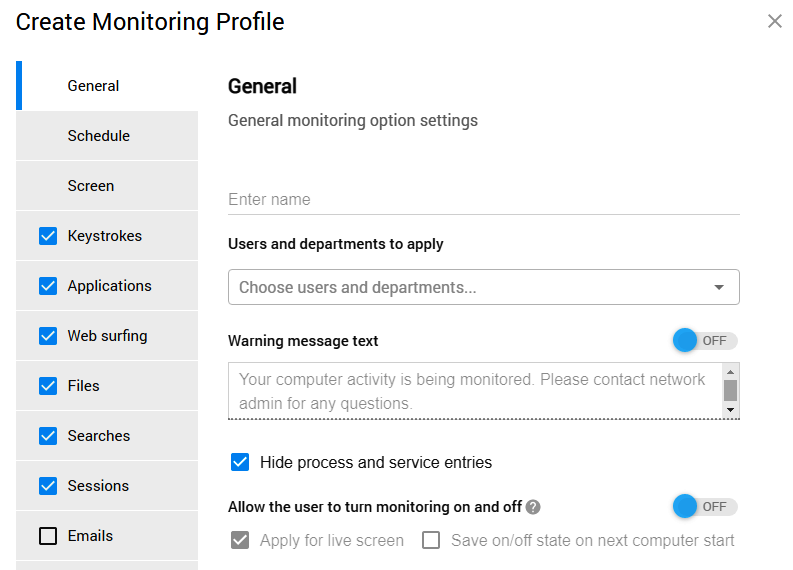
However, do not take Work Examiners products as the way to spy on your staff, exactly as your IUP shouldn’t be overly restrictive. It’s better to use employee monitoring software to highlight areas that need to be addressed for building strong organizational culture and a healthy working environment.
Share a post
Start to monitor employees instantly!
Install our solutions all over your network within 5 minutes