WEBlog - discover interesting things about your employees.
All posts
Why Employers Should Monitor Windows Activity and the Best Tools They Can Use

When you equip your staff with brand-new computers, you don’t expect the employees to load the machines with video games, use the Internet access in the workplace for socializing on Facebook, or manipulate files and systems they are not authorized to enter. In fact, your desktops can tell a lot about who and how actually uses workplace devices. And since the lion’s share of them comes with Microsoft’s OS, it makes sense to learn what activity you can monitor in Windows and why you really need to do this.
Why Do You Need to Monitor Windows Activity?
The first thing that comes to mind is your workforce’s performance. Surely, the Internet alone can be a powerful distraction dragging productivity down. As far back as the beginning of the 2000s, a study showed that productivity lost due to the World Wide Web cost $63 billion to US businesses and 9.6 billion to organizations in the UK annually. As the Internet has spread even wider from that time, we suspect that things got only worse.
However, the consequences of computer misuse by employees are not limited to productivity drops. It is telling that another research revealed higher employers’ concern about data leaks and security breaches than about workplace distractions. Namely, approximately 50% of the respondents specified portable storage misuse, unauthorized software downloading, and the usage of remote access programs, P2P file-sharing, and insecure Wi-Fi access points/modems as primary threats. At the same time, only 14% of the participants believe they should panic about non-work web browsing.
Indeed, an employee transferring confidential data to a memory stick can force your company into a data breach scandal leading to multimillion losses. Downloading programs from unreliable sources can easily let a piece of malware into your systems. By visiting innocent-looking websites, your staff puts you in danger of hacker attacks, while content downloaded from P2P file-sharing platforms may violate copyright regulations, followed by lawsuits. From sexual harassment channeled through emails to company records destroyed by rough employees, business owners face multiple risks associated with their Windows-powered computers. So, it would be only fair to check your system at least from time to time, and we are here to tell you where to look.
Activities to Monitor in Windows
The good news is that the Windows system and popular web browsers are provided with helpful features that don’t require you to be a computer geek for deriving some information through them. But employers often ignore these opportunities because they are too obvious. Well, sometimes, keeping it simple is the best way to go.
Check the browsing history
Google Chrome, Opera, Firefox, Microsoft Edge, and Internet Explorer — all the browsers store their history in the tab of the same name. To see it, you should click on:
- the three-dot menu in the top right corner for Chrome
- the Opera icon in the upper left-hand corner for Opera
- the hamburger menu at the upper right-hand corner for Firefox
- the Settings button next to the address bar for Microsoft Edge
- the star icon at the upper right for Explorer
Depending on the browser’s functionality, you will be able to look through the web pages visited, use a search bar for easier hunting, and even observe browsing history from devices attached.
Look into the Google account
This search engine tracks almost any online activity even if you use a different browser than Chrome while staying connected to your Google account. Moreover, the accounts are linked to multiple services like Google Maps or Google Drive. This gives you a nice chance to check search history, watch history on YouTube, search queries, comments, and posts generated from your workplace computers provided your employees don’t bother to switch between personal and work-related Google accounts.
Launch the search engine on the desktop in question and do the following:
- Press the App Launcher icon (known as Waffle in everyday language) in the top right corner of the screen.
- Enter the account and proceed to Data & Personalization.
- Scroll down to the Activity and timeline panel to see the apps used, web search history, YouTube views, activities performed on websites, and more.
Mind, however, that Google can show you only that part of the history you allowed it to store. Go to Activity controls to change settings if you want the search engine to collect a wider set of data.
Rifle through the Recycle Bin
It’s time to switch from online history to offline activities monitored by Windows itself. The Recycle Bin help learn what files were deleted and when (which can lead you to the person who did it) and for restoring documents that may be critical for your workflow. Surely, a smart rough employee would clean the bin, but files can be deleted accidentally, not to mention that some violators are not actually smart.
Search for modified files
If you suspect that one of your team members accesses documents not related to their tasks or performs non-work activities like playing computer games during working hours, you can either confirm or refute the suspicions by viewing recently modified files. You need to do the following:
- Right-click on the Start menu and find the Run button.
- Type in “recent” in the bar and press OK.
- Go through the files shown to spot suspicious activities.
Since a malicious user can clean this folder, you have another way to observe recent modifications to files — through Windows/File Explorer (This Computer – Search Bar – Search Tools – Date Modified).
Explore downloads
As previously mentioned, anything downloaded from unauthorized sources can do damage to your business. So, you’d better keep track of downloads by inspecting the dedicated Windows folder. It is simple to find with the help of Windows/File Explorer in the Quick Access list on the left tab. Even if someone has emptied it, you will be aware of the problem.
Examine programs launched and installed
An insight into software pieces your staff uses delivers three sets of information:
- whether there are any security threats you should know about;
- if the software usage complies with copyright regulations;
- which programs are most frequently used and which don’t pay off.
Here are the steps you should follow to get this info:
- Go to This computer through Windows/File Explorer.
- Type “.exe” in the search bar.
- Right-click on any heading to get into Details.
- Tick Date Modified and save it.
- Select the Date Modified column to see when the program in question was started or dig deeper into its location and type.
You can also check when an app was installed on the desktop by entering Control Panel and moving to Programs and Features. Here, you need to press the Installed On column to get the list of programs conveniently sorted.
Gauge the performance of your computer
Too many programs installed and launched can overload workplace desktops and reduce their performance. With Windows Task Manager, it is possible to identify the software and processes that consume an extra amount of the CPU, disk space, memory, and network resources, as well as possible hidden requests from unauthorized applications, for example, malware.
Although Task Manager can be entered in plenty of ways, we would recommend the "Ctrl + Shift + Esc" key combination, which allows jumping directly to the desired tool, including when using a remote desktop or a virtual machine. However, you may prefer the "Ctrl + Alt + Delete" option or other alternatives to get the same result.
How to Monitor Windows Activity with Work Examiner
As you can see, multiple tools are designed to provide employers with useful data about their workplace computers usage. Yet, you may find it difficult to cope with so many solutions since neither of them delivers exhaustive information. On the contrary, Controlio by Work Examiner covers numerous activities performed on Windows-based devices, with no need for you to learn how different browsers or Windows versions work. Since all the information is collected in a single user-friendly dashboard, you can save time and effort while exploring:
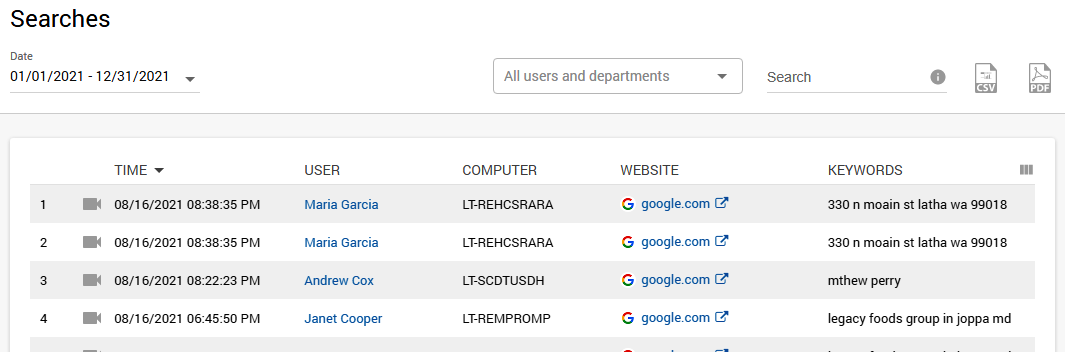
Online searches
You don’t need to tinker with search engines, as Controlio displays queries inserted in any of them for each user and department. You can look through the report and immediately see phrases that have nothing to do with the tasks assigned or even those related to searching for adult content, gambling sites, and so on.
Websites visited
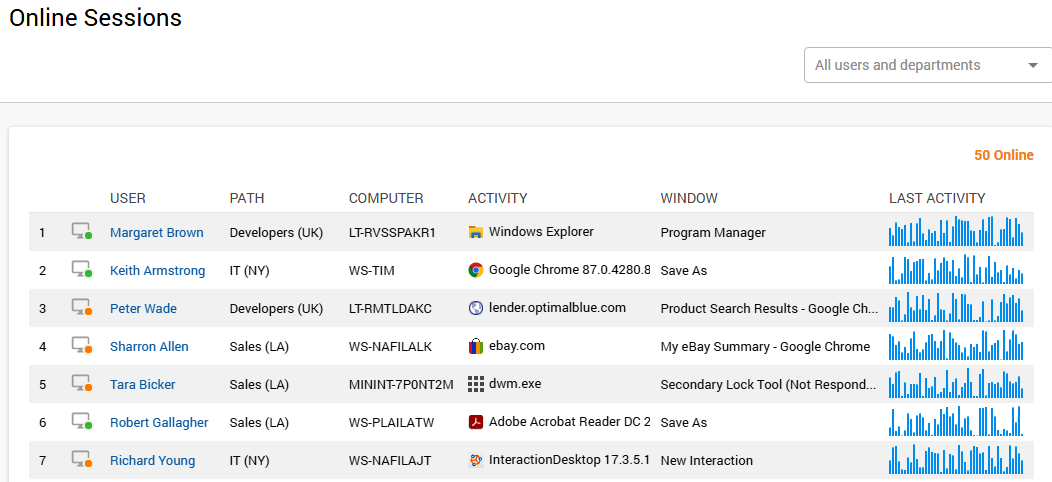
In the Online Sessions tab, Controlio shows all users who are currently online. The real-time information includes computers used, websites and apps launched, and even live streaming videos capturing the screens.
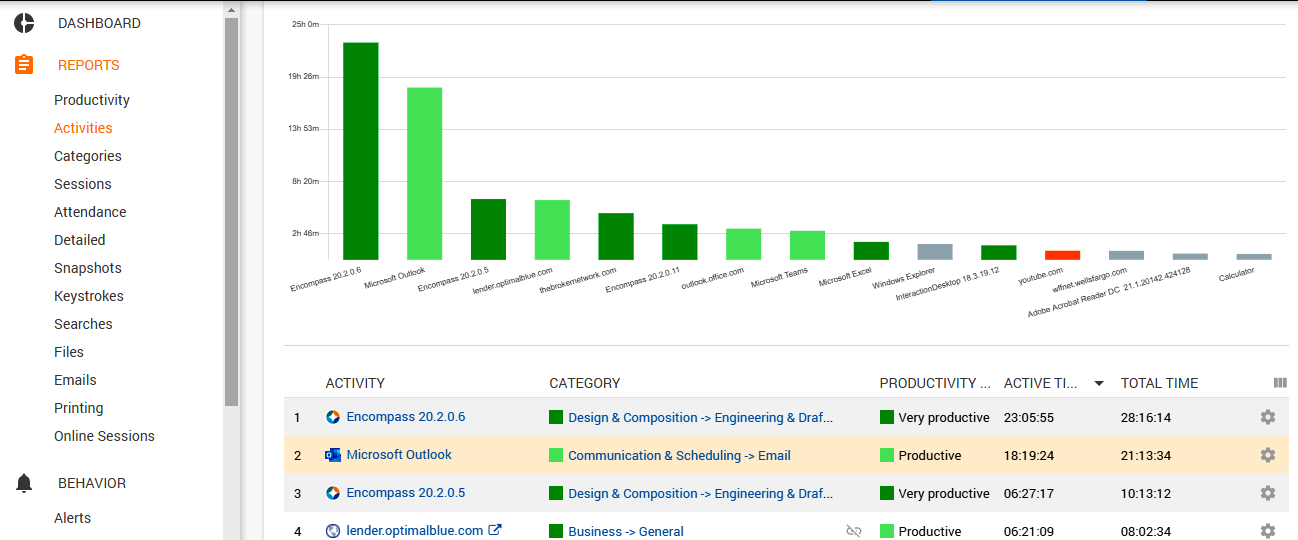
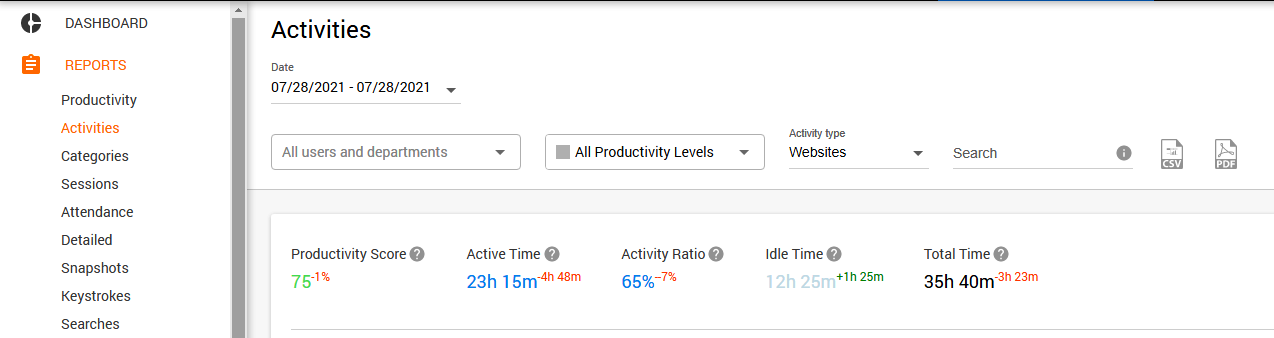
Moreover, the Activity tab widget will give a broader picture of the web platforms visited by your staff. It sorts the websites by productivity levels, which are easily customized right in this section, and aggregates vital benchmarks like a total productivity score, productivity graph, and more.
Applications put to work
The employer can check what applications are used by the staff in various ways. Online Sessions display the usage of apps in real-time, while the Activity tab will deliver historical data — you need to select Applications in the Activity type settings.
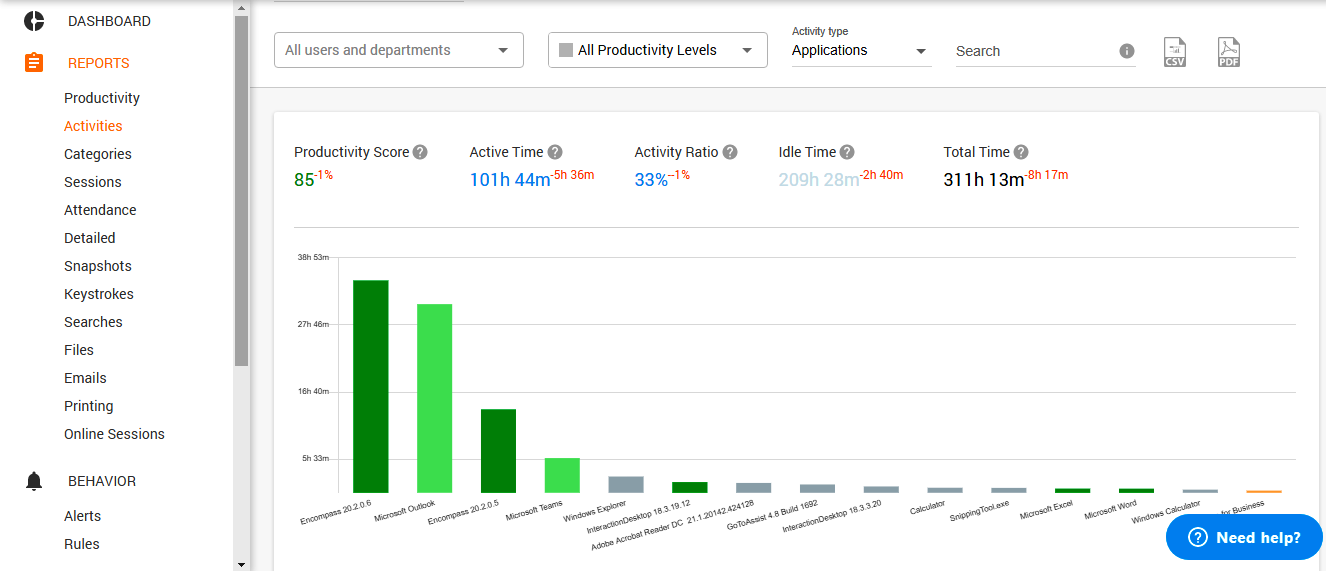
Further, both web and app usage is represented in easy-to-grasp visuals on the dashboard so that you could explore the most frequently used solutions right away.
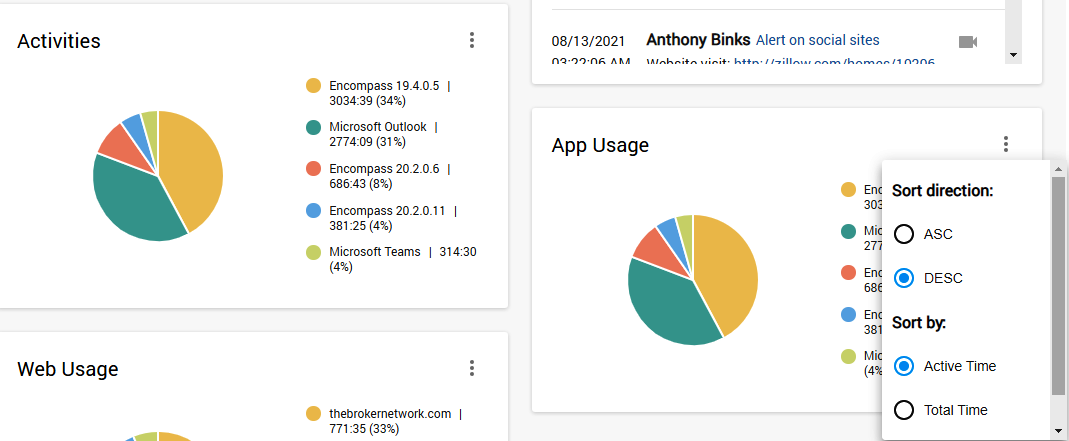
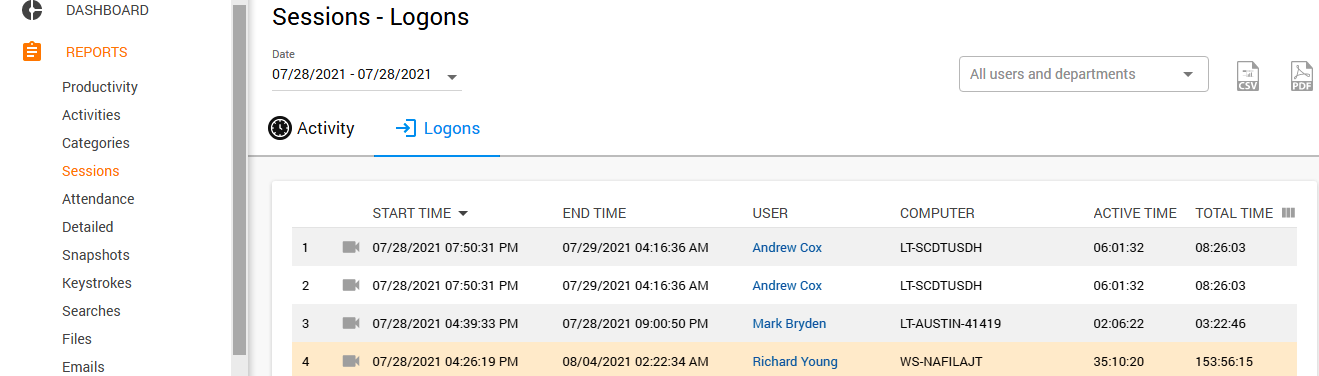
Logons
By going to the Sessions tab and choosing Logons, you will be able to find out when your employees start and end using workplace computers. Active and Total times attached to this report explain whether your team members do their jobs after the sessions begin or they are distracted by something.
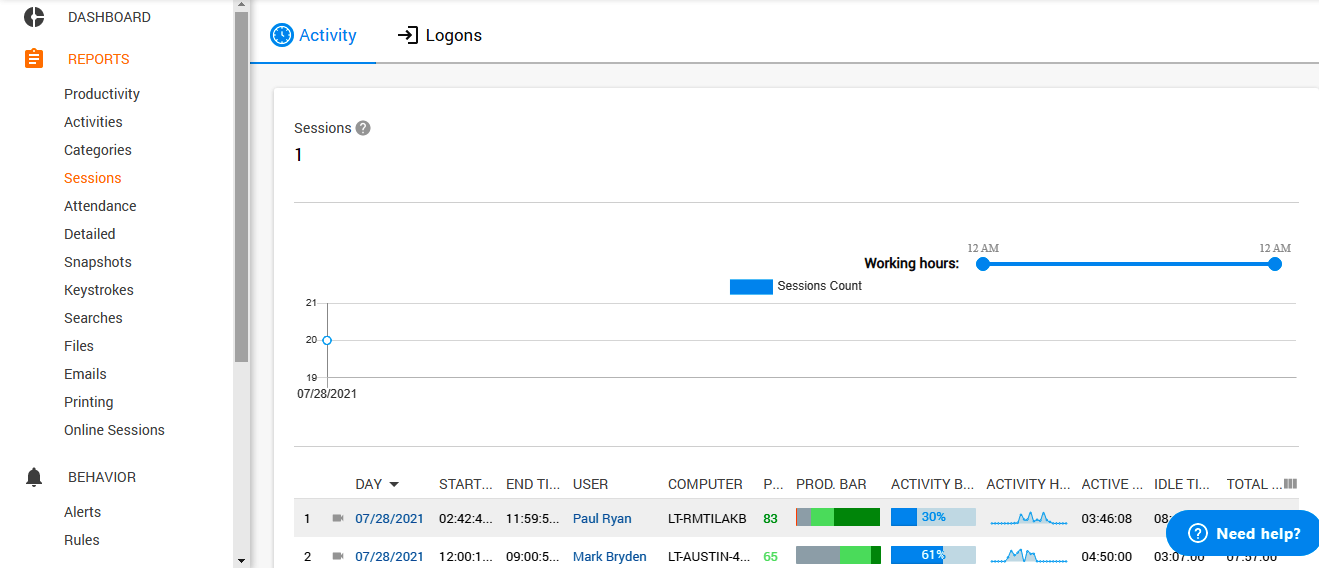
The Activity button in the same tab provides you with more detailed information on that, bringing together productivity parameters, activity hours, and total time.
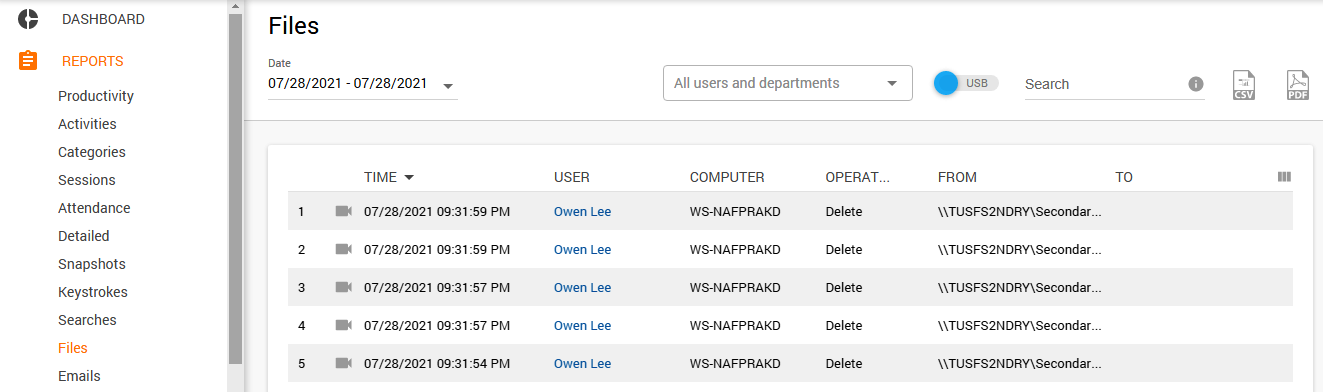
Operations with files
Now you can forget about Windows brain busters, as the File widget of Controlio works perfectly to let you know about any action performed with files on each of your computers. It saves the time, user, activity type, and path if a document is moved somewhere, for example, transferred to a memory stick.
The described features have given you an idea of how Controlio is beneficial for monitoring your workplace desktops, but Work Examiner’s tools have much more to offer.
Share a post
Start to monitor employees instantly!
Install our solutions all over your network within 5 minutes