WEBlog - discover interesting things about your employees.
All posts
How to Nail a Rogue Employee Before It’s Too Late

A report published by Cybersecurity Insiders says that 90% of organizations feel vulnerable to damaging activities performed by insiders. What's worse, more than half of them suffered from insider attacks within a year before the survey, which proves that their fears are anything but irrational. Although authorized clients and partners may also pose certain risks, employees remain the most probable source of the threat. And here we bump into the rough employee problem, meaning you might have an enemy within your organization. How to detect this ticking bomb prior to its explosion? Let’s see into Work Examiner’s solutions helping to elicit the problem and take meaningful actions for protecting your business.
Sharing Corporate Data with Competitors
Problem:
You might be naïve enough to believe that business espionage is something shown in Hollywood action films only. But the results of one poll conducted among 4,000 employees in Europe, the US, and Australia can serve as a wake-up call for you: one-third of the participants were ready to sell confidential corporate data to competitors if offered a good price. Moreover, 3% of them were not really greedy and would settle for as little as £100. The sum is so miserable that we have every reason to suspect rough employees in those participants — they are concerned with doing a bad turn to their companies rather than earning some bucks. The question is how much it would cost your business.
Solution:
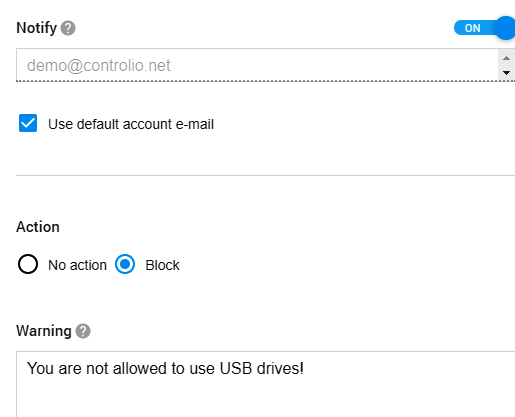
Getting USB flash drives under control is only one of the ways to prevent data leakage with the help of Controlio. You just need to go to the Behavior Rules section, click on Create, and select Insert Removables from the Event Type list.
Then, you can specify users or departments that have access to valuable information like a client database or earnings reports while limiting a circle of trusted staff members via the Except option. All the rest will be prohibited from using USB drives, thus having no chance to transfer the data from your computers. In addition, the software will notify you about the attempt and display a warning message to remind your employees of company policies. It’s an easy solution for cutting off at least one common channel of a data leak.
Another channel that can be brought under control is printing out. Controlio will deliver reports on all the documents sent to printing devices connected to your computers.
Defaming a Company Through Social Media
Problem:
While the number of global social media users is approaching 4 billion, many companies are undertaking earnest efforts to establish their presence on Facebook or Twitter. While social networking sites are instrumental in achieving various business goals, from improving brand awareness to increasing leads, they have the equal power to ruin your company or cause colossal losses. Think of the UK’s Metro Bank losing 11% of its stock value in the midst of a panic caused by false WhatsApp messages about the bank’s financial problems. Now, suppose that your rogue employee is somewhere there posting compromising information about your company. Not good, isn’t it?
Solution:
With Work Examiner’s monitoring tools, you can track the social media activities of your employees to prevent them from sharing damaging materials, at least in the workplace. Through the Activities section, you can learn which of your staff members spends much time on Facebook and, what is more important, whether they just browse their friends’ pages.
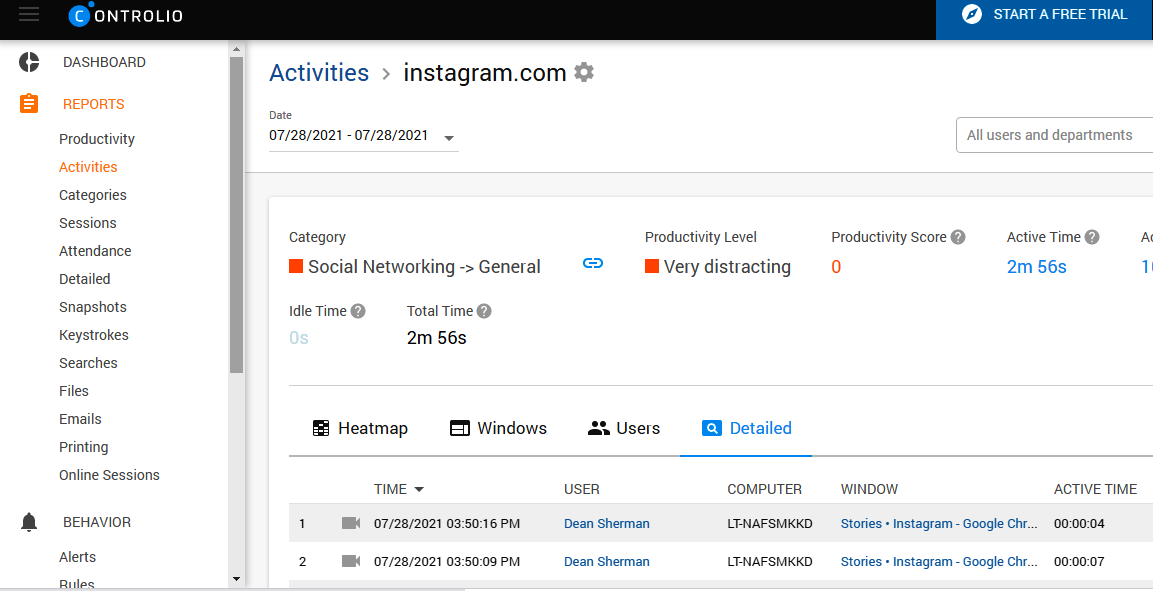
Press the camera icon to open a window with video recordings and observe the screen with the whole content the employee sees.
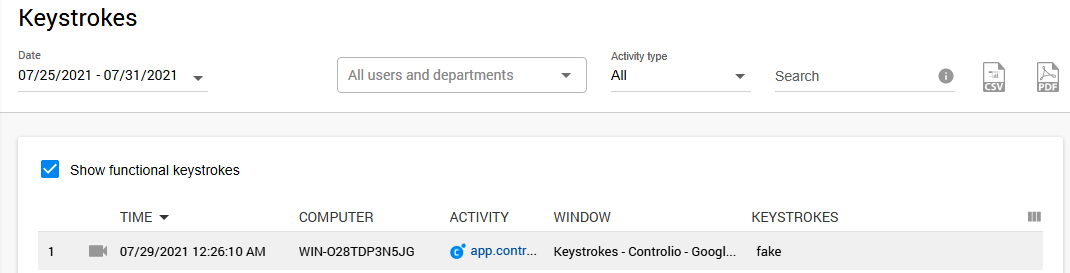
Further, you can avail of configuring alerts notifying you about certain keystrokes made by your workers. For example, type in the name of your company and get a warning each time a user mentions it so that you could switch to screen monitoring and check in what context your business is referred to.
Surely, you can make a list of multiple words, including offensive language or phrases related to your company’s sensitive info, which will also help you tackle other possible issues with a rogue employee. If you suspect someone spreads fake news or posts negative reviews about your
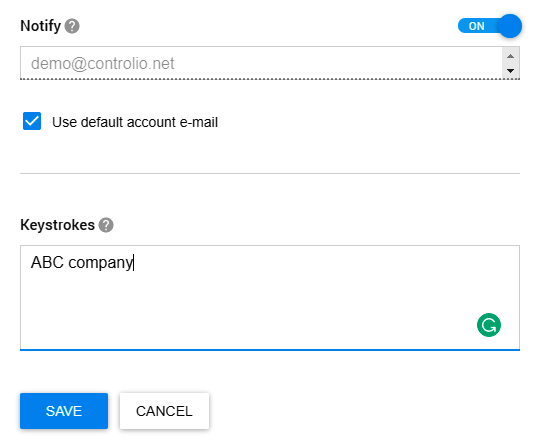
company, you can catch the person red-handed by exploring the Keystrokes section and searching for the evidence by user, activity, or words.
Destroying Corporate Data
Problem:
The name of Scott Arledge became public after the former senior vice president at PharMerica in Tampa had been accused of deleting the company’s data stored on his work computer two days prior to his resignation. As a result, PharMerica lost 475 files and went to court, claiming that it was deprived of the benefit of the information contained in those documents. But the problem is even bigger since rough employees are not bound to wait until dismissal to start ruining your business. Actually, it is even more convenient for them to access your critical data while still on board.
Solution:
Obviously, you need to restrict access to the most sensitive info, but here is one more idea on how you can spot the problem. With Controlio, you are welcome to monitor files processed by your staff and observe suspicious activities they may perform. The Files section of your dashboard will show you who, what, and when; so, if something goes wrong, you will know it.
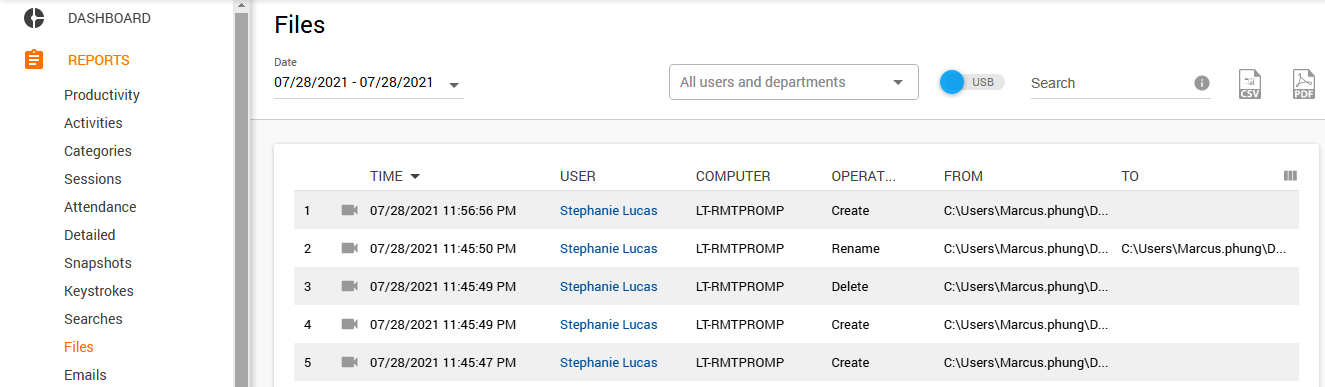
What is more, screen records available for each activity will provide you with evidence if your suspicions turn out to be true. They will also come in handy to clarify dubious situations and advocate the fair name of wrongly accused employees.
Conclusion
We have outlined only a couple of possibilities offered by Work Examiner for identifying a rogue employee before he or she could do much harm to your business. You can also avail of these features to reach other goals, such as boosting productivity, adjusting corporate policies, or preventing multiple security threats. Either way, this employee monitoring software pays off, guiding your business through the challenges of digitalization.
Article Photo © Tim Pierce | Flickr
Share a post
Start to monitor employees instantly!
Install our solutions all over your network within 5 minutes